Amazon.co.jp: Bluetooth Speaker, v5.1 Wireless Speaker, Luminous Speaker, Bluetooth, 20 Hours Playback, Small, LED Light, For iPhone, Android, Smartphone, PC, Lightweight, TV, Car, Heavy Bass, Multiple Connections : Electronics

Blue Ant X4 Bluetooth speaker review: Price, sound quality, party mode, best bluetooth speaker? Worth it? | A multi-speaker party at the press of a button

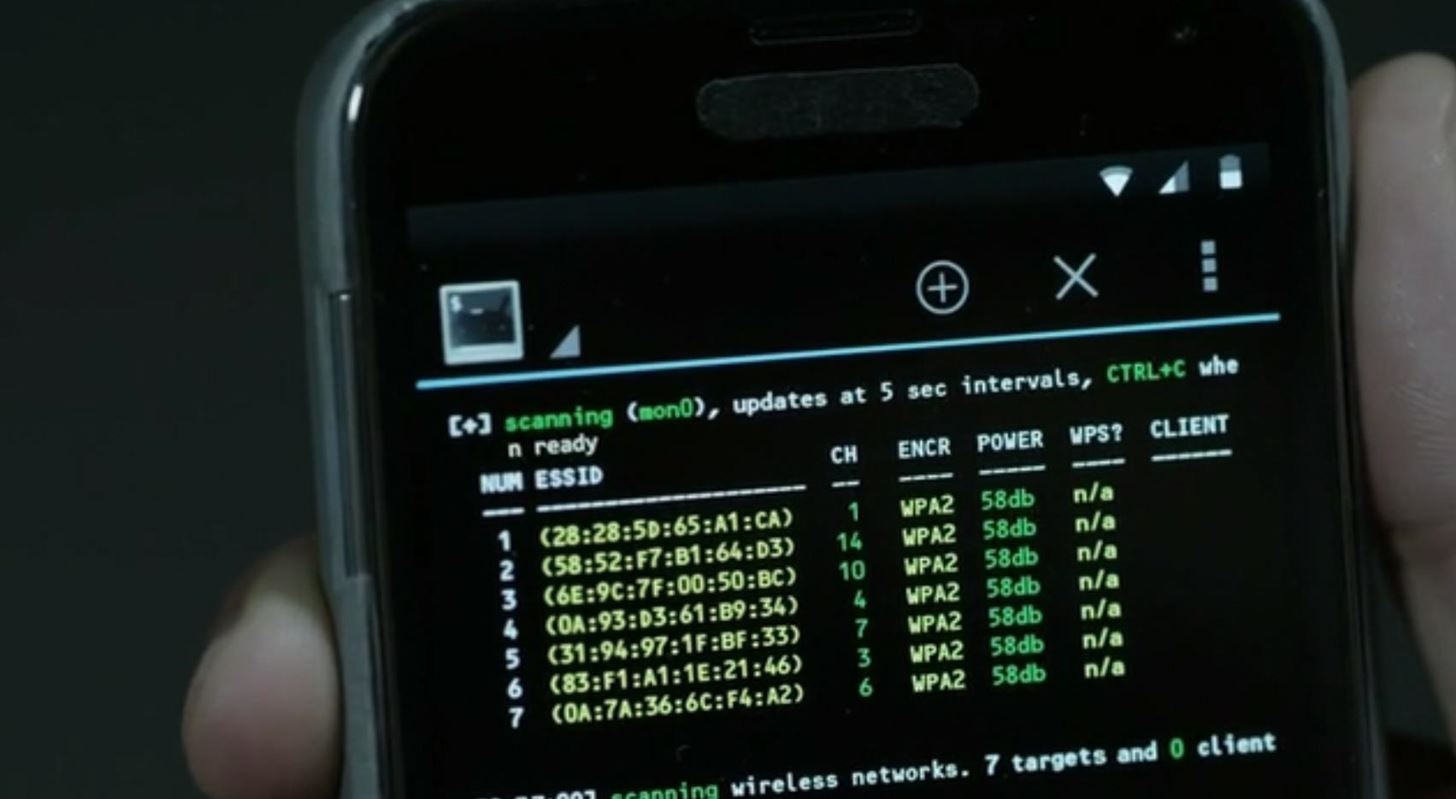
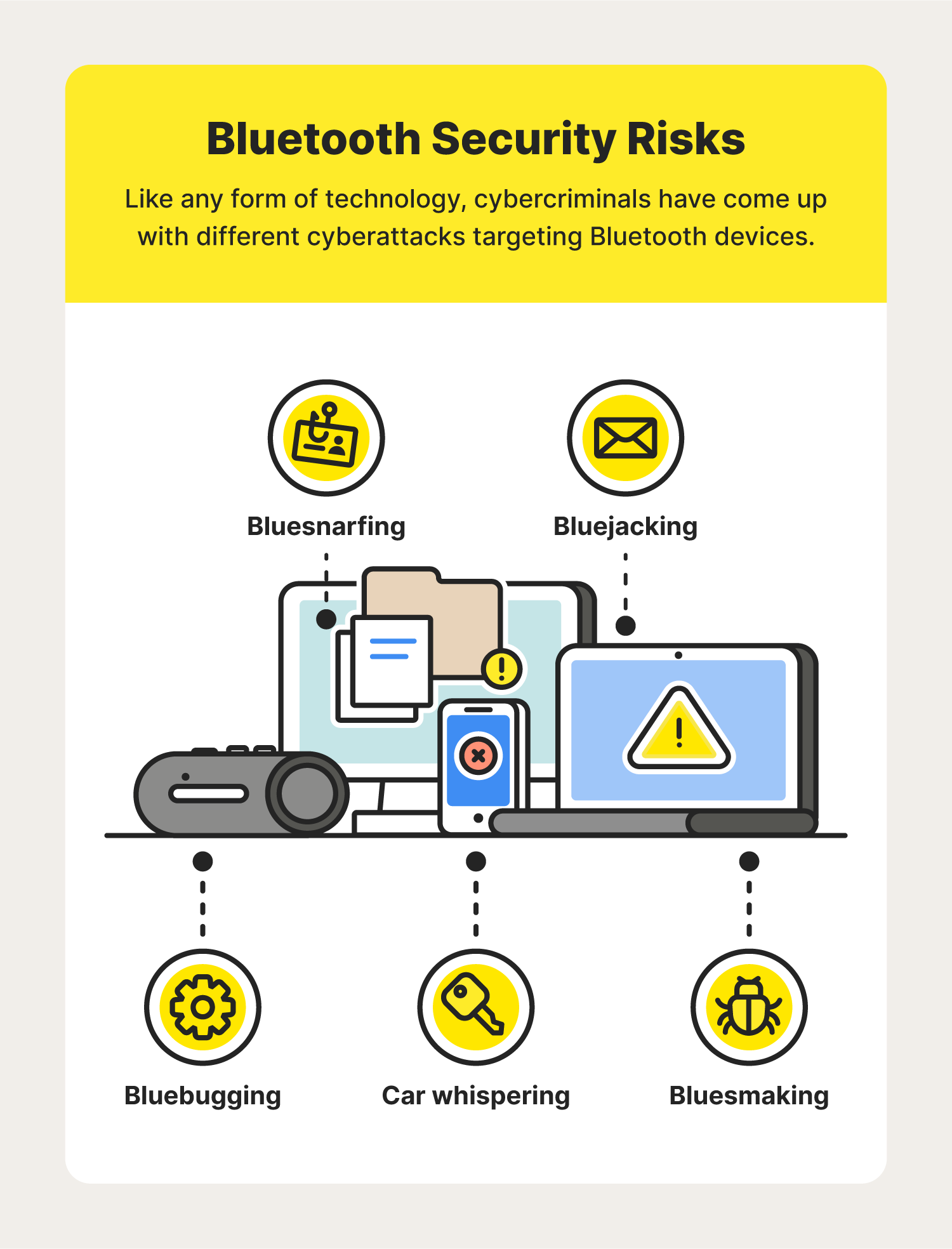
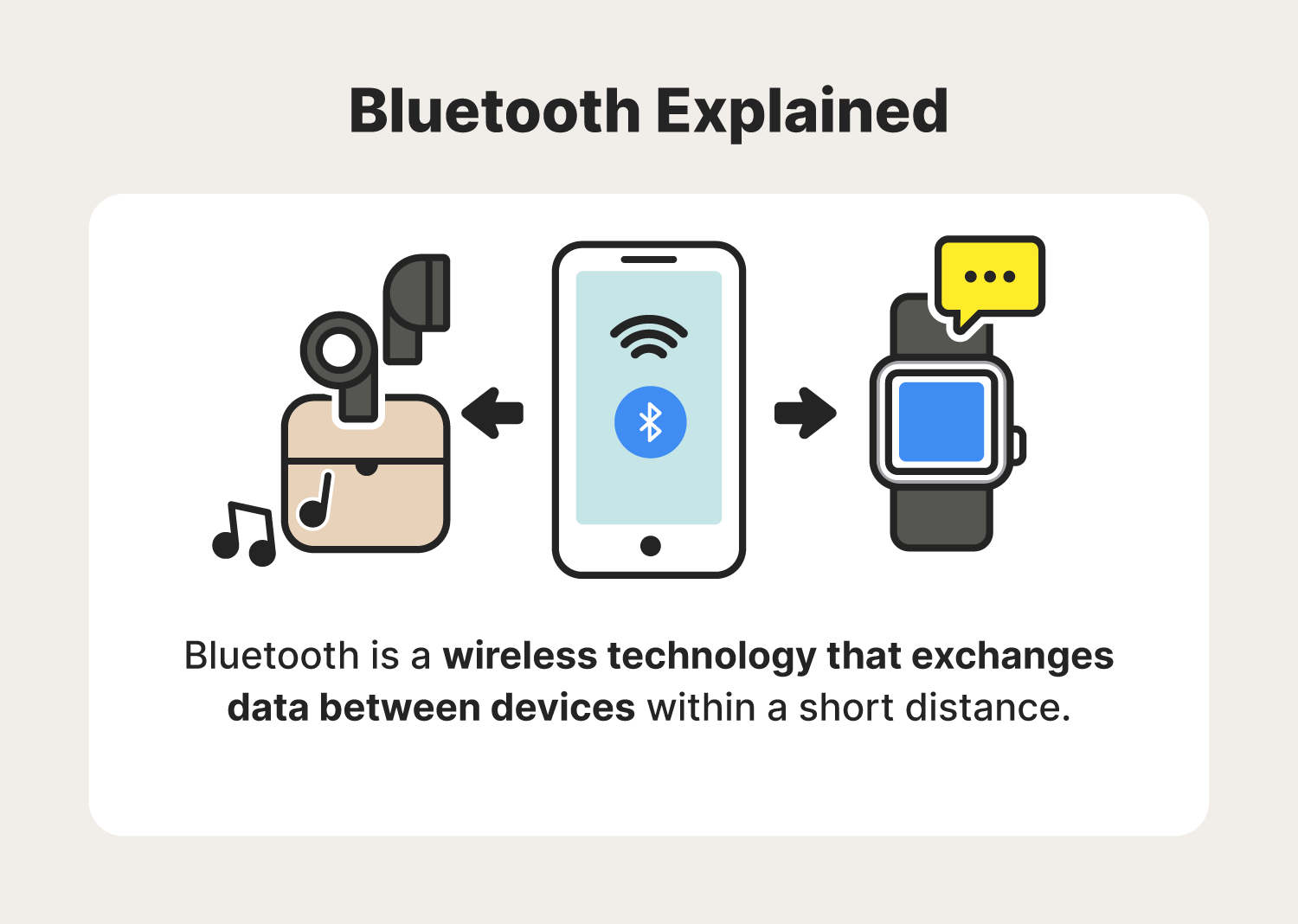
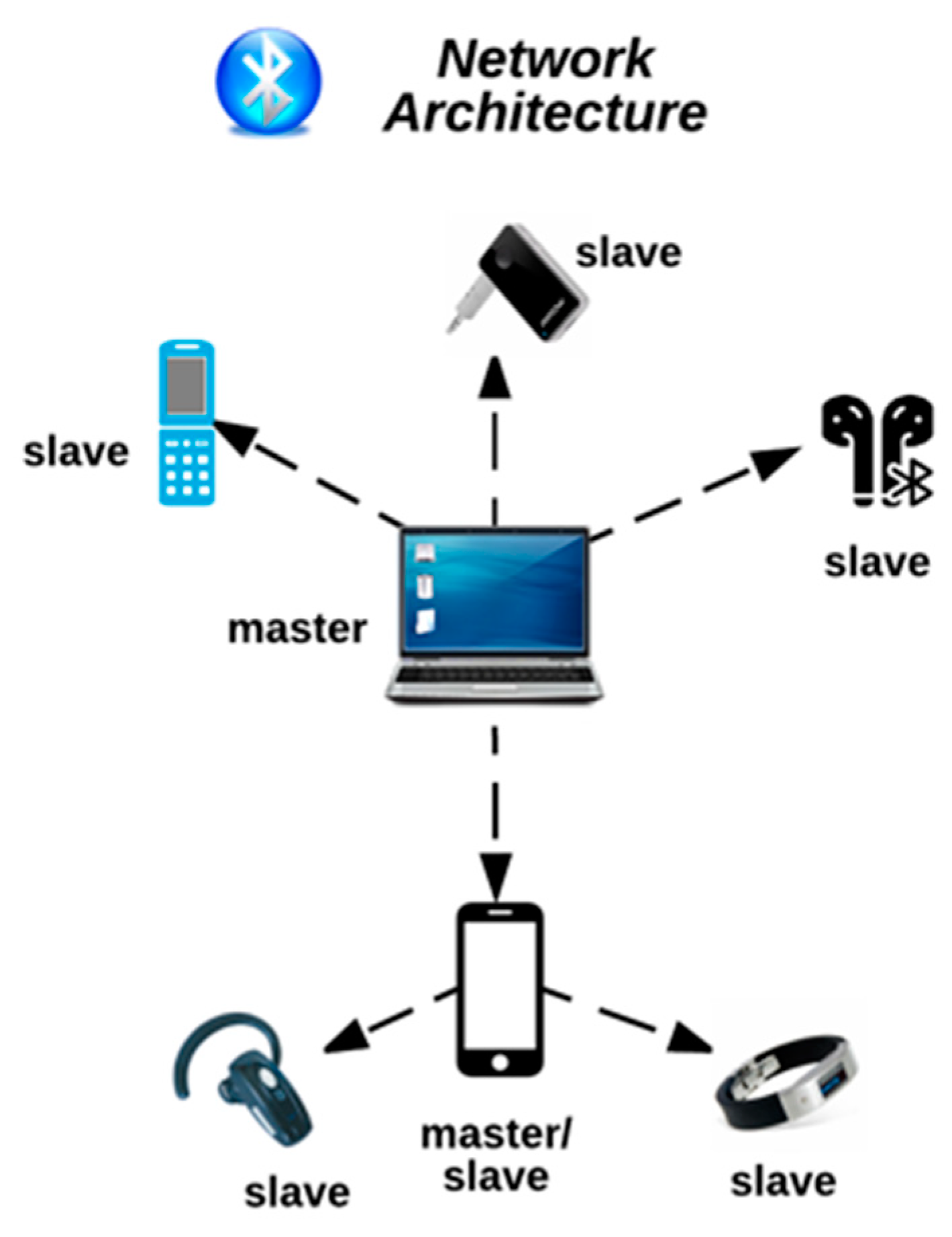
How to Hijack a Bluetooth Speaker? (Basic and Advanced Methods) | Bluetooth speaker, Bluetooth speakers, Bt speaker