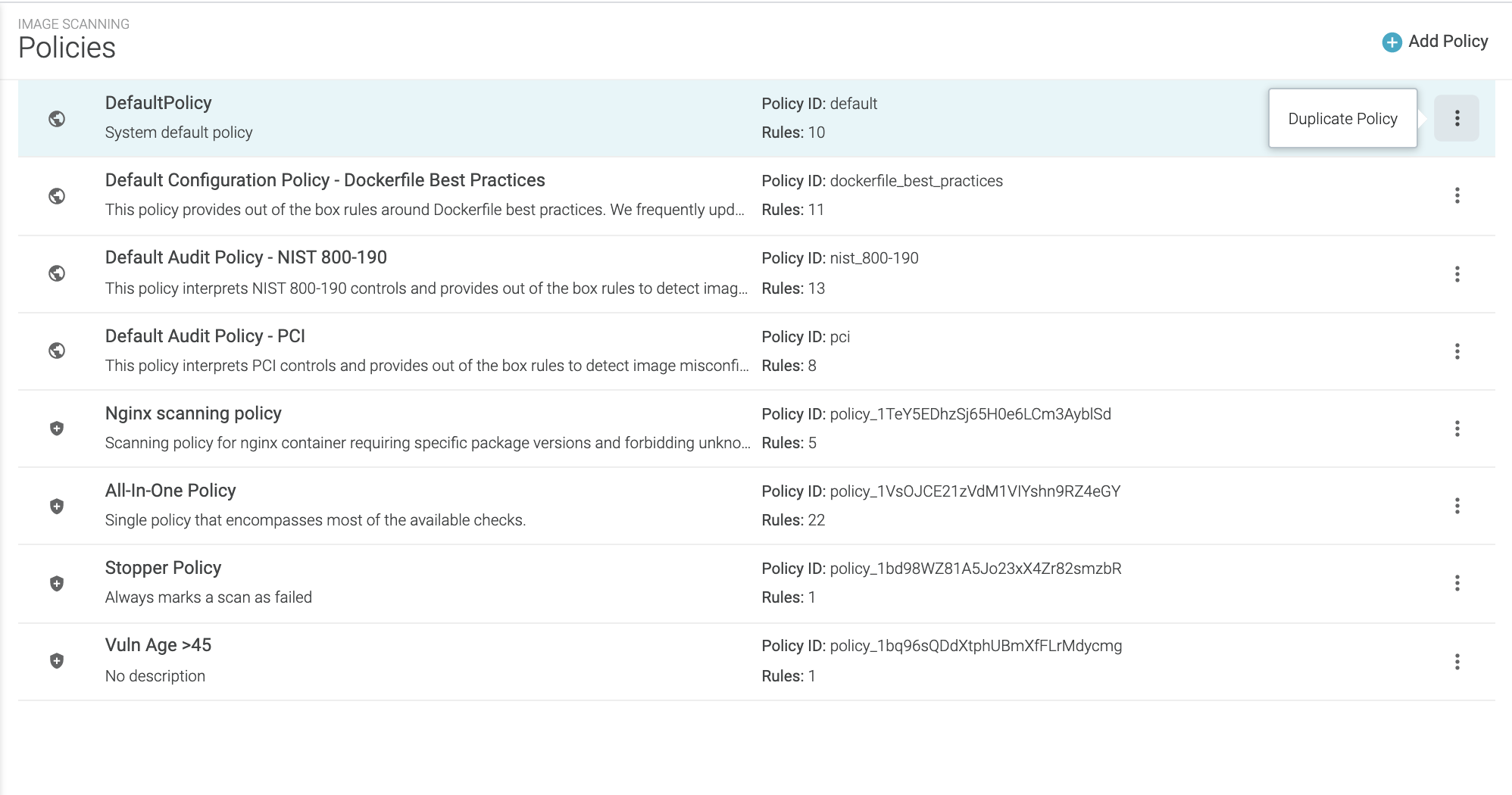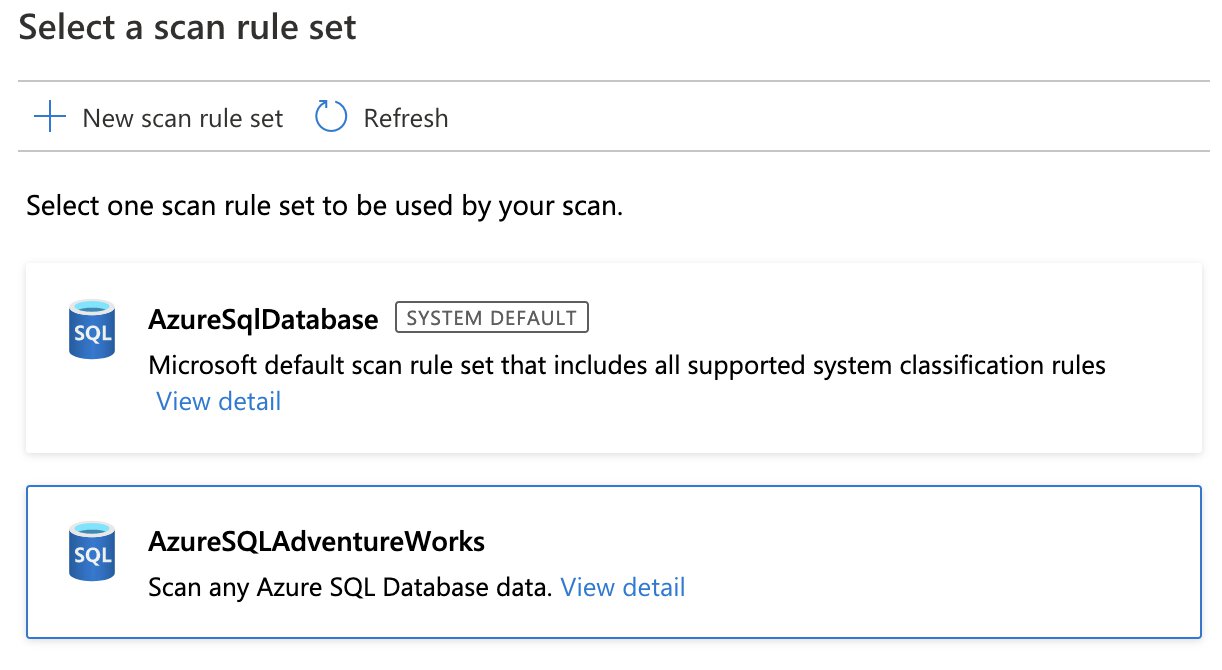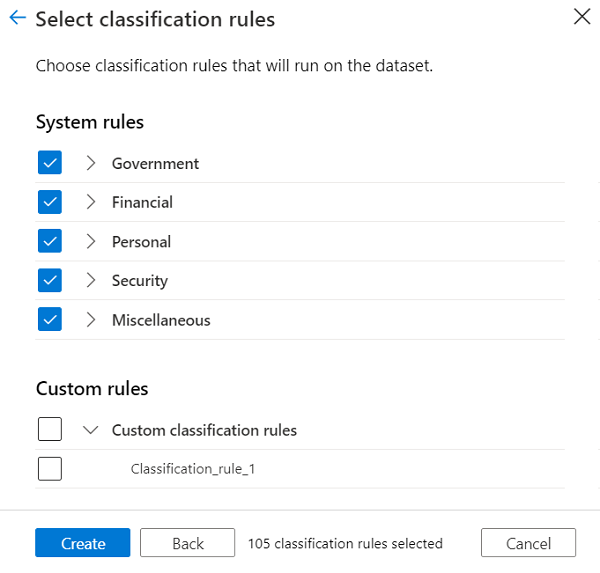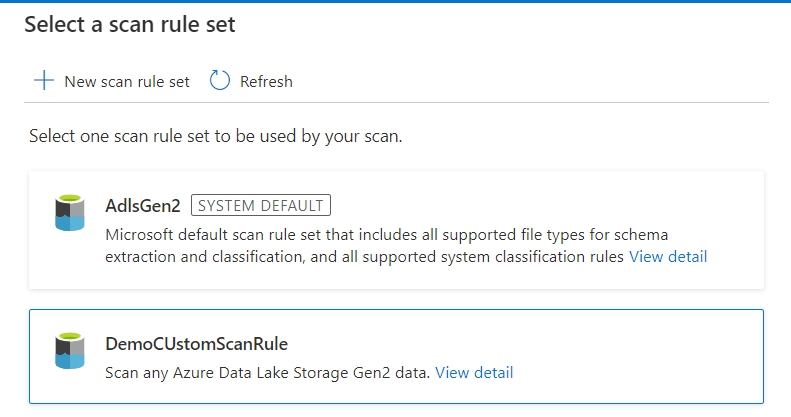
Quick overview of Purview. Recently I have been looking into… | by Subhasree Mohapatra | Jan, 2024 | Medium
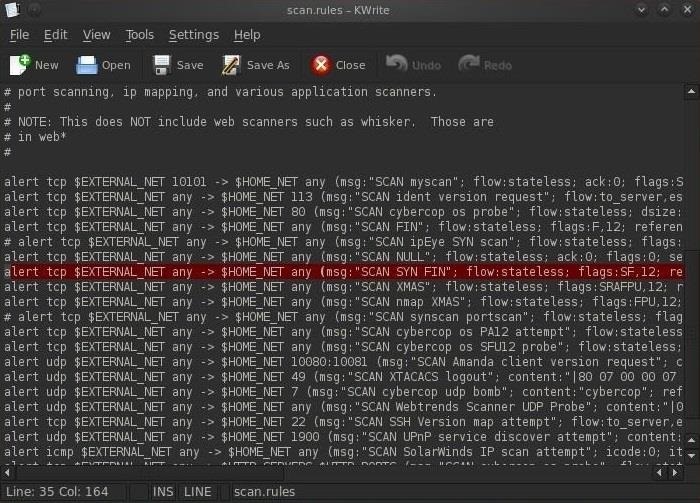
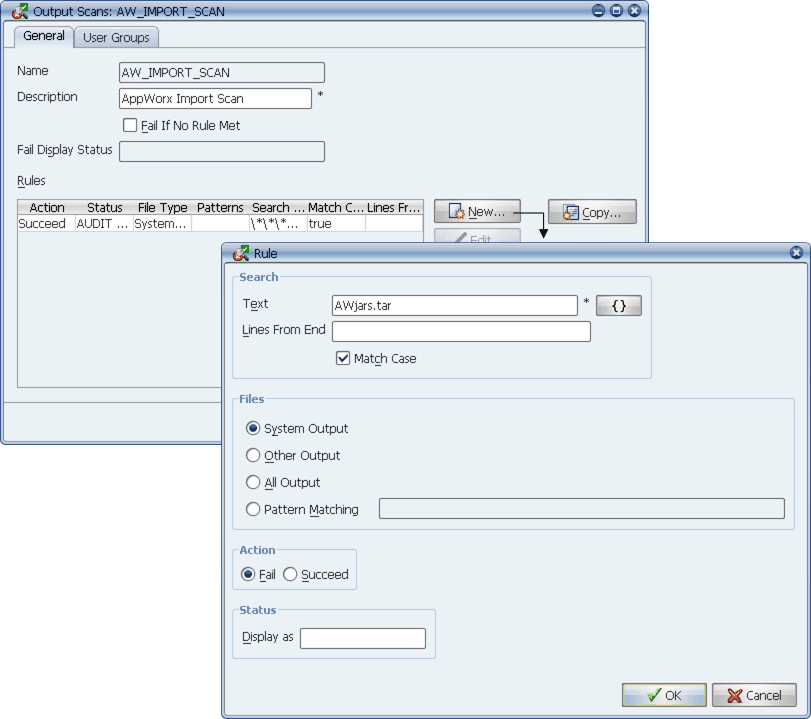
Hack Like a Pro: How to Read & Write Snort Rules to Evade an NIDS (Network Intrusion Detection System) « Null Byte :: WonderHowTo

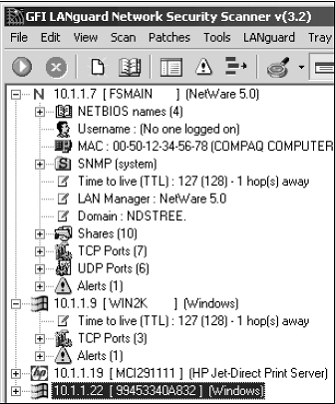
Figure 6 from Rule-Based Network Intrusion Detection System for Port Scanning with Efficient Port Scan Detection Rules Using Snort | Semantic Scholar

1 Lecture 23 Design for Testability (DFT): Full-Scan n Definition n Ad-hoc methods n Scan design Design rules Scan register Scan flip-flops Scan test sequences. - ppt download
![PDF] Rule-Based Network Intrusion Detection System for Port Scanning with Efficient Port Scan Detection Rules Using Snort | Semantic Scholar PDF] Rule-Based Network Intrusion Detection System for Port Scanning with Efficient Port Scan Detection Rules Using Snort | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ce0229f8e85305f52e759d172b00adecc626dbbc/5-Figure4-1.png)